Google Hacking/Dorking Explanation By Sajawal Hacker
It involves using specialized search query operators to finetune results based on what you are looking for.
- Google Dorks one of most easy, fun, and powerful hacking techniques, online.
- On the Internet, Websites are not only to be hacked, Websites are just part of the Internet.
- There are many other products like Refrigerator, CCTV Cameras, Automated Doors, Televisions, Power Plants, etc. that are connected to the Internet, and some of them could be accessed through google.
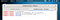
- inurl:”CgiStart?page=”
- inurl:/view.shtml
- intitle:”Live View / – AXIS
- inurl:view/view.shtml
- inurl:ViewerFrame?Mode=
- inurl:ViewerFrame?Mode=Refresh
- inurl:axis-cgi/jpg
- inurl:axis-cgi/mjpg (motion-JPEG) (disconnected)
- inurl:view/indexFrame.shtml
- inurl:view/index.shtml
- inurl:view/view.shtml
- liveapplet
- intitle:”live view” intitle:axis
- intitle:liveapplet
- allintitle:”Network Camera NetworkCamera” (disconnected)
- intitle:axis intitle:”video server”
- intitle:liveapplet inurl:LvAppl
- intitle:”EvoCam” inurl:”webcam.html”
- intitle:”Live NetSnap Cam-Server feed”
- intitle:”Live View / – AXIS”
- intitle:”Live View / – AXIS 206M”
- intitle:”Live View / – AXIS 206W”
- intitle:”Live View / – AXIS 210?
- inurl:indexFrame.shtml Axis
- inurl:”MultiCameraFrame?Mode=Motion” (disconnected)
- intitle:start inurl:cgistart
- intitle:”WJ-NT104 Main Page”
- intitle:snc-z20 inurl:home/
- intitle:snc-cs3 inurl:home/
- intitle:snc-rz30 inurl:home/
- intitle:”sony network camera snc-p1?
- intitle:”sony network camera snc-m1?
- site:.viewnetcam.com -www.viewnetcam.com
- intitle:”Toshiba Network Camera” user login
- intitle:”netcam live image” (disconnected)
- intitle:”i-Catcher Console – Web Monitor”
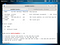
- inurl:"view/indexFrame.shtml"
- inurl:"view/index.shtml"
- intitle:"Live View / - AXIS"
- intitle:axis camera
- intitle:"axis #Kameramodell#"
- inurl:sample/LvAppl/
- intitle:"V.Networks [Motion Picture(Java)"
- intitle:"EvoCam"
- inurl:"webcam.html"
- intitle:"my webcamXP server!"
- inurl:/control/userimage.html
- inurl:/ViewerFrame?Mode=Motion
- inurl:toolam.html
- inurl:viewash.html
- intitle:"TOSHIBA Network Camera - User Login"
- inurl:/home/homeJ.html
- inurl:/view.shtml
- intitle:”Live View / - AXIS” | inurl:view/view.shtml^
- inurl:ViewerFrame?Mode=
- inurl:ViewerFrame?Mode=Refresh
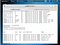
- inurl:axis-cgi/jpg
- inurl:axis-cgi/mjpg (motion-JPEG)
- inurl:view/indexFrame.shtml
- inurl:view/index.shtml
- inurl:view/view.shtml
- intitle:”live view” intitle:axis
- intitle:liveapplet
- allintitle:”Network Camera NetworkCamera”
- intitle:axis intitle:”video server”
- intitle:liveapplet inurl:LvAppl
- intitle:”EvoCam” inurl:”webcam.html”
- intitle:”Live NetSnap Cam-Server feed”
- intitle:”Live View / - AXIS”
- intitle:”Live View / - AXIS 206M”
- intitle:”Live View / - AXIS 206W”
- intitle:”Toshiba Network Camera” user login
- intitle:”netcam live image”
- intitle:”i-Catcher Console - Web Monitor”
- intitle:start inurl:cgistart
- intitle:”WJ-NT104 Main Page”
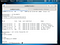
- intext:”MOBOTIX M1? intext:”Open Menu”
- intext:”MOBOTIX M10? intext:”Open Menu”
- intext:”MOBOTIX D10? intext:”Open Menu”
- intitle:snc-z20 inurl:home/
- intitle:snc-cs3 inurl:home/
- intitle:snc-rz30 inurl:home/
- intitle:”sony network camera snc-p1?
- intitle:”sony network camera snc-m1?
⚠️Nᴏᴛᴇ:- Tʜɪs ᴀʟʟ ɪɴғᴏʀᴍᴀᴛɪᴏɴ ᴘʀᴏᴠɪᴅᴇᴅ ʙʏ ᴜs ɪs ᴏɴʟʏ ғᴏʀ ᴍᴀᴋᴇ ʏᴏᴜ ᴍᴏʀᴇ ᴀᴡᴀʀᴇ ᴀɴᴅ sᴇᴄᴜʀᴇ ғʀᴏᴍ ᴛʜɪs ᴛʏᴘᴇ ᴏғ ʜᴀᴄᴋɪɴɢ ᴏʀ ᴄʀᴀᴄᴋɪɴɢ ᴀɴᴅ ɪғ ʏᴏᴜ ᴜsᴇ ɪᴛ ɪɴ ɪʟʟᴇɢᴀʟ ᴘᴜʀᴘᴏsᴇ ᴛʜᴇɴ ᴡᴇ ᴀʀᴇ ɴᴏᴛ ʀᴇsᴘᴏɴsɪʙʟᴇ ғᴏʀ ᴛʜᴀᴛ !
➖➖➖➖➖➖➖➖➖➖➖➖
👍ʜᴏᴘᴇ ʏᴏᴜ ɢᴜʏs ʟɪᴋᴇ ᴛʜɪs ᴘᴏsᴛ.
"please give your feedback in comment"